Which of the Following Statements Correctly Describes Biometric Methods
2 i The following identifiers of the individual or of relatives employers or household members of the individual are removed. Which of the following statements correctly describes the practices regarding customer privacy in the US.
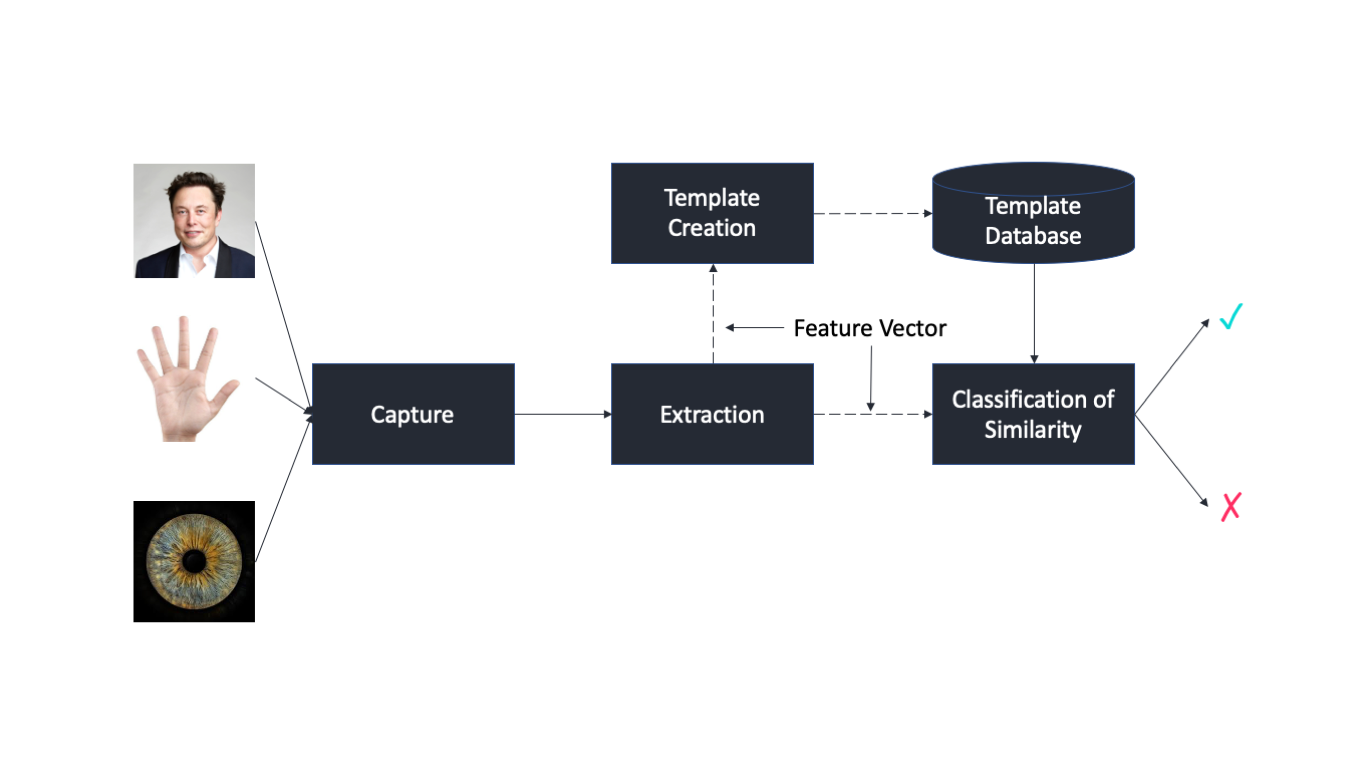
Biometric Authentication Methods Fingerprints Facial Recognition Hand By Anh T Dang Towards Data Science
Face biometrics use aspects of the facial area to verify or identify an individual.

. Biometrics Comparison Facial Recognition Fingerprint Recognition Iris Recognition Palm Vein Recognition Voice Authentication. Biometrics make good authenticators because you must have an exact match to the computer. Finger geometry is a biometric process that captures features such as the shape and surface area of each finger its length width.
In 164514 b the Safe Harbor method for de-identification is defined as follows. Which of the following is the authentication method used here. Which of the following statements best describes a customer lifetime value CLV.
Which of the following statements is true about biometrics as an authentication method. Biometrics are based on the Type 2 authentication mechanism. 104-Which of the following is the WEAKEST authentication mechanism.
They are the least expensive and provide the least protection. They are the most expensive and provide the most protection. Analyze the following statements and select the statement which correctly explains the difference between cross-site scripting XSS and cross-site request forgery XSRF.
They are the least expensive and provide the most protection. Biometrics are the most secure kinds of authenticators. Add a sequence flow to an end event after the discard errors activity.
Which of the four Ps describes the. Which of the following statements correctly describes the disadvantage of a hardware-based keylogger. It uses a microchip loaded with identifying data to authenticate users d It provides weak authentication compared to other methods.
It is easy to duplicate and transfer someone elses fingerprints using biometrics. Physiological biometrics b Cognitive biometrics Behavioral biometrics d Security key authentication 15 ns 9. A software application identifies specific points of data as match points.
An algorithm is used to process the match points and translate that information into a numeric value. Consider the following BPMN diagram of a subprocess. This graphic covers which of the following.
Which of the following methods should enable the organization to. Which of the following items are not supported as a method of authentication in Windows 10. Digital certificates smart cards picture passwords and biometrics are used to perform which of the following actions.
Biometrics verifies individuals based on who they are ie. It uses personal physical characteristics for authentication It is less invasive than other methods of authentication. HTTP is an example of a protocol handled at the Application layer of the OSI model.
When comparing biometric systems a low false acceptance rate is most important when security is the priority. These steps are taken to convert the biometric input for identity verification. 102-Which of the following statements pertaining to biometrics is FALSEUser can be authenticated by what he knows.
Biometrics are based on the Type 3 authentication mechanism. Which of the following statements correctly describes biometric methods. Computer scientists are always.
OSI is a set of rules that describes how security devices stop attacks. Whereas a low false rejection rate is most important when convenience is the priority. They are the most expensive and provide the least protection.
Type 1 is something you know type 2 is something you have. In the US personal information is generally viewed as being in the public domain and retailers can use it in any way they desire. Top Five Biometrics Face Fingerprint Iris Palm and Voice Modalities Comparison.
XSRF spoofs a specific request against the web application while XSS is a means of running any arbitrary code. Some systems use very high FARs such as 1 in 300. 103-Which of the following biometric devices offers the LOWEST CER.
The OSI session layer handles connections between applications while the transport layer handles connections between systems. Consider biometric methods that are used to authenticate a user. An accounting information system AIS is defined as being an information system that records processes and reports on transactions to provide financial information for decision making and control.
The characteristics inherent to the individuals. All biometric implementations balance these two criteria. A low Crossover-Error-Rate CER D.
105-Which of the following statements pertaining to access control is false. Which of the following is true about biometric authentication. Type 3 is something you are.
Knowing that errors are possible which of the following would most likely result in a security breach. Guidance on Satisfying the Safe Harbor Method.

Which Of The Following Statements Correctly Describes Biometric Methods Skillset
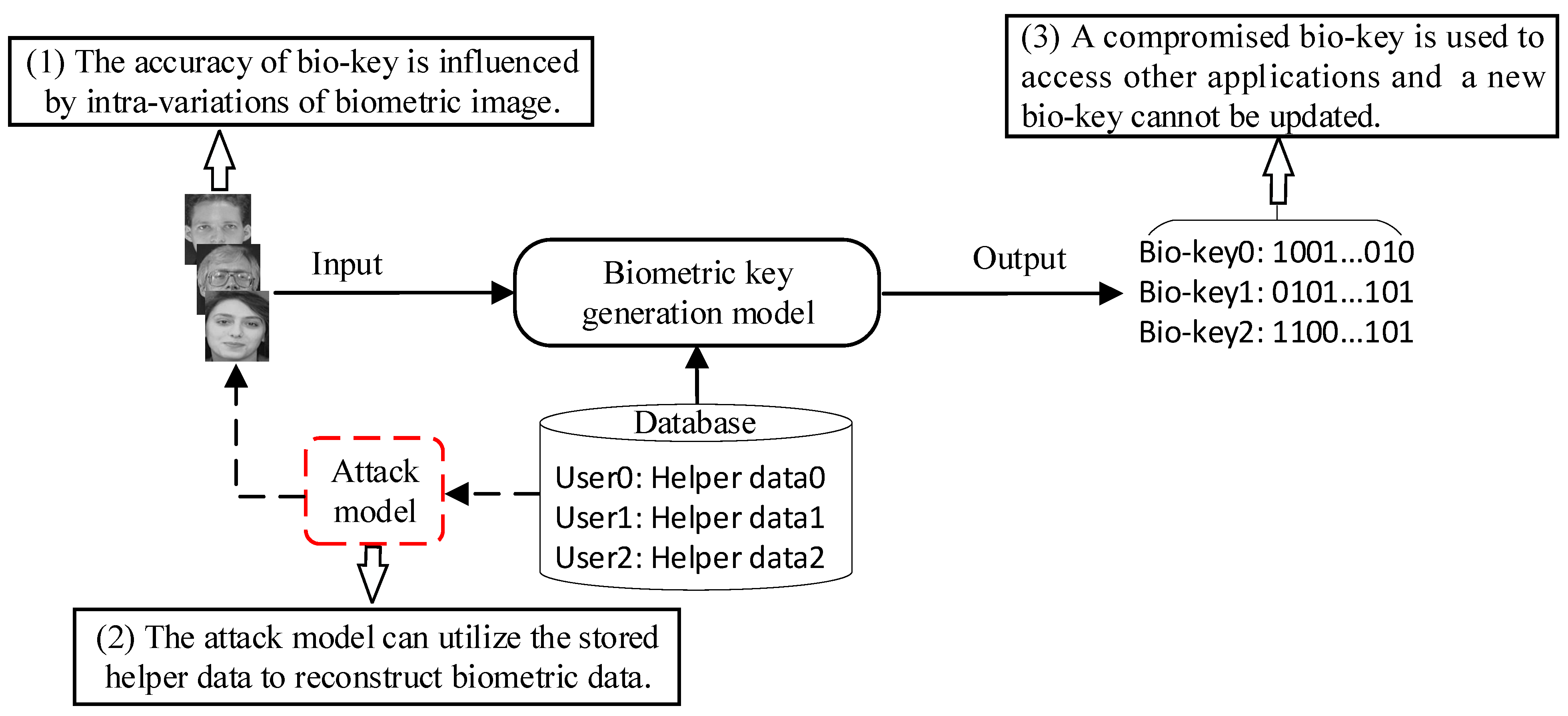
Applied Sciences Free Full Text A Secure Biometric Key Generation Mechanism Via Deep Learning And Its Application Html

Comments
Post a Comment